Everything published in this article is just for educational purposes and for “white” knowledge, that is the knowledge used only for defense. Respect the programmers’ work. In general, use the knowledge you get from resources like this, to create more robust programs or better protecting tools.
According to Wikipedia: Software cracking is the modification of software to remove or disable features which are considered undesirable by the person cracking the software, usually related to protection methods: (copy protection, protection against the manipulation of software), trial/demo version, serial number, hardware key, date checks, CD check or software annoyances like nag screens and adware. (http://en.wikipedia.org/wiki/Software_cracking)
What You Will See
In this article you will learn what is required in order to start thinking as a cracker. I will show the least elementary steps needed for cracking simple programs.
I am going to give you two examples of how to crack a “home-made” program just to take the idea of what is behind in both parts: the cracker and the programmer. Next, I will show how to crack a small and simple commercial program. This program is no longer available (at least in the version that it was when it was cracked).
In general, you will learn:
• What we think when we crack.
• What knowledge we have to have.
• What tools we can use.
What you should know
• Basic knowledge of Assembly language (http://en.wikipedia.org/wiki/Assembly_language).
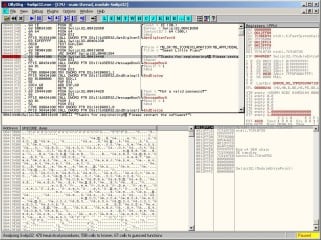
• An idea of how debuggers and disassemblers work and specially Olly debugger (Figure 1 and http://www.ollydbg.de/).
• Hex editors (you have to know at least what it is – http://en.wikipedia.org/wiki/Hex_editor).
• Basic knowledge of Machine Registers (http://en.wikipedia.org/wiki/Processor_register).
• Also, welcome (and many times required) is the knowledge of PE executables internal structure (http://en.wikipedia.org/wiki/PE_executables).
• Programming skills are always welcome ;)
Figure 1. Olly: A well-known PE executable’s debugger
Let’s Crack
Everything published in this article is just for educational purposes and for “white” knowledge, that is the knowledge used only for defense. Respect the programmers’ work. In general, use the knowledge you get from resources like this, to create more robust programs or better protecting tools.
Target #1: The “un-pressable” Button
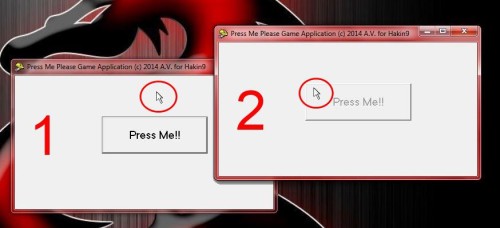
Our first target is a program that programmers used to create for fun. A window appears and prompts the user to press a specific button, but when the mouse pointer comes over, the button becomes disabled (Figure 2).
Figure 2. Press the button… if you can!
Sometimes, programmers used this trick when they realize that a user use the program in a not legitimate manner (unregistered, illegal copy etc.). Thus, the existed button “Start” (in every application’s welcome screen) becomes disabled when the user try to press it!
The key here, for the cracker, is how to find a way to fool the application in order to allow the user to press the button before (or after…?) the program disable it. Here, we need some programming knowledge, a hex editor and (as always) some… tricky thoughts.
The method that we are going to use is the following: From elementary Windows programming we know that if we prefix any letter of any Caption Text Component with the ampersand symbol (&) the current letter becomes a shortcut to activate the component! Well…, this is the trick. We will change the caption “Press Me” of the main button of the application to “Press&Me”. This means that the user will see the caption as “PressMe” which means that the letter M is a shortcut for this button, which means that if he/she pressed the keys Alt+M is the same thing as he/she pressed the button itself.
[raw] [/raw]
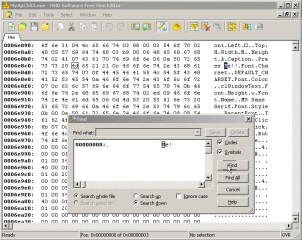
The question now is how to change the caption of the button without access to the source code of the program. The answer is a Hex Editor. We open the executable program with a hex editor (Figure 3).
Figure 3. Using a hex-editor we can see the machine instruction of a program as hexadecimal numbers
What we see here can be divided into three parts that corresponds to the three columns that the cracker sees. The 1st column is the address of the current machine instruction, the 2nd column is the machine instruction itself in hexadecimal format and the 3rd column is (again) the machine instruction in raw text format or better, its text representation.
In Figure 3 you can see my first step, which is to find the text “Me!” in the text representation column. What is needed is to change the words “Press Me” (see the 3rd column) to “Press&Me”, and save the file (using the same name – or in a different name if you want to keep a backup).
Let’s now run the program and press Alt+M (Figure 4). So easy, huh?
Figure 4. Press Alt+M and voila, the buttons is pressed without touching it ;)
Target #2: My Sweet Little Piano
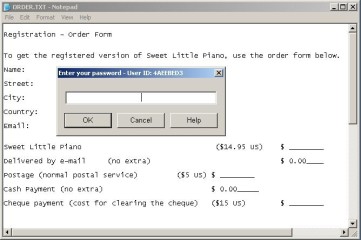
It is time now to go a step further. We are going to bypass the registration control of a simple commercial application: the “Sweet Little Piano”. The actual executable file is called Swlipi32.exe. This application converts our keyboard to a piano. The “problem” is that it requires a small amount of money in order to release all of its features.
When the program starts, asks for a password and (in addition) it displays a banner with some financial requirements of how to order, etc. (Figure 5).
Figure 5. The welcome screen of the Sweet Little Piano
I press OK without entering any password, I get an error message: “Not a valid password!”. This message is the key of my method to bypass the protection. What I am going to do is:
• I will use the Olly Debugger to open the program.
• I find the machine instructions that correspond to the command that display the message “Not a valid password!”
• Near to the display command a check for a correct password must exist.
• I will modify the password check instruction in order to skip this check and…
• That’s it!
Ok, nice with the theory, let’s do the real thing now.
I use File | Open in Olly and I load the executable Swlipi32.exe. My first job then is to locate the string “Not a valid password!” (Figure 1). But wait, before proceed please let me explain to newcomers to Olly Debugger what we see in this Figure 1. The Olly window is divided into 4 parts:
• The top-left part shows the assembly instructions of the program.
• The top-right part displays the value of the machine registers.
• At bottom left and
• At Bottom right are the contents of the current running program’s memory (heap, stack) that we are not going to use (at least) in this article.
To find the string “Not a valid password!”, I right click on the Top Left Part of the Olly window and I select “Search For -> All Reference Text Strings”. Olly will respond with a new window with all machine instructions found containing the above string. The window has three columns: the Address, the Dissasembly and the Text String column. I am interested on the last one. So, I found the line (below):
Address Disassembly Text string
00401384 PUSH Swlipi32.00414428 ASCII “Not a valid password!”
I double Click on this line and Olly redirects me to the program’s corresponding instructions, here:
00401352 . 68 90904100 PUSH Swlipi32.00419090 ; |Title = “Sweet Little Piano”
00401357 74 2B JE SHORT Swlipi32.00401384
00401359 . 68 40444100 PUSH Swlipi32.00414440 ; |Text = “Thanks for registering! Please …
0040135E . 56 PUSH ESI ; |hOwner
0040135F . FF15 A0434100 CALL DWORD PTR DS:[<&USER32.MessageBoxA>>; MessageBoxA
00401365 . 6A 01 PUSH 1 ; /Result = 1
00401367 . 56 PUSH ESI ; |hWnd
00401368 . C705 88BA4100 >MOV DWORD PTR DS:[41BA88],1 ; |
00401372 . FF15 98434100 CALL DWORD PTR DS:[<&USER32.EndDialog>] ; EndDialog
00401378 . B8 01000000 MOV EAX,1
0040137D . 5E POP ESI
0040137E . 83C4 60 ADD ESP,60
00401381 . C2 1000 RETN 10
00401384 > 68 28444100 PUSH Swlipi32.00414428 ; |Text = “Not a valid password!”
00401389 . 56 PUSH ESI ; |hOwner
0040138A . FF15 A0434100 CALL DWORD PTR DS:[<&USER32.MessageBoxA>>; MessageBoxA
00401390 . 6A 01 PUSH 1 ; /Result = 1
00401392 . 56 PUSH ESI ; |hWnd
00401393 . C705 88BA4100 >MOV DWORD PTR DS:[41BA88],0 ; |
0040139D . FF15 98434100 CALL DWORD PTR DS:[<&USER32.EndDialog>] ; EndDialog
004013A3 . B8 01000000 MOV EAX,1
004013A8 . 5E POP ESI
004013A9 . 83C4 60 ADD ESP,60
The line 00401384 (or better, the address) is responsible for displaying the message of password failure:
00401384 > 68 28444100 PUSH Swlipi32.00414428 ; |Text = “Not a valid password!”
The current message of failure could be the start of our success ;) If you check a few addresses above, at address 00401359, you can see a very interesting message: “Thanks for registering! Please… “.
00401359 . 68 40444100 PUSH Swlipi32.00414440 ; |Text = “Thanks for registering! Please …
The program here Thanks the user for registering. It is very possible that very near a “jump to an address” is located that the program redirects the user, after a successful registration. Indeed there is such instruction, at address 00401357:
00401357 74 2B JE SHORT Swlipi32.00401384
If case you wonder what the above instruction means in English then read this:
IF THIS = THAT THEN GOTO ADDRESS 00401384.
We know (from above) that the address 00401384 is the address of a wrong password. So, in pure English, we have the following situation here:
IF THE PASSWORD IS WRONG THEN DISPLAY ERROR MESSAGE.
I will make the following trick: I will change the above logic to:
IF THE PASSWORD IS CORRECT THEN DISPLAY ERROR MESSAGE.
This means that if the password is WRONG, the program will skip this instruction and will continue execution to the immediate next instruction, meeting the address 00401359 which is the address “Thanks for registering”! To do this I will change the instruction at address 00401357 from JE (Jump If Equal) to JNZ (Jump if Not Equal):
00401357 74 2B JΝΖ SHORT Swlipi32.00401384
I am Double-Click to instruction “JE SHORT Swlipi32.00401384” and Olly displays a window with the current instruction. I just change the JE to JNZ and I press Assemble. This means that when the user enters a wrong password the programs will behave as it was correct! This situation has a funny side-effect: If we are so… “unlucky” and the password we enter is the real one, then we get an error message…! Well, in such case try another password and/or go to play in an online lottery as well… ;)
But, we are not finish yet! The registration form still appears when the application starts (even it gives us now all of its features). We should get rid of this annoying form. Hmm… if you are observant enough (and you should be if you want to be a good reverser) you will realize that the order form located in a file with the name order.txt. So, let’s start search for the word “order.txt” in the Olly Debugger. I found it, at this address:
004018C0 /$ 8B4C24 04 MOV ECX,DWORD PTR SS:[ESP+4]
….
004018EC |.^75 F7 JNZ SHORT Copy_of_.004018E5
004018EE |> 6A 01 PUSH 1 ; /IsShown = 1
004018F0 |. 8D5424 04 LEA EDX,DWORD PTR SS:[ESP+4] ; |
004018F4 |. 52 PUSH EDX ; |DefDir
004018F5 |. 6A 00 PUSH 0 ; |Parameters = NULL
004018F7 |. 68 30454100 PUSH Copy_of_.00414530 ; |FileName = “order.txt”
004018FC |. 68 28454100 PUSH Copy_of_.00414528 ; |Operation = “open”
00401901 |. 6A 00 PUSH 0 ; |hWnd = NULL
00401903 |. C64404 19 00 MOV BYTE PTR SS:[ESP+EAX+19],0 ; |
00401908 |. FF15 24424100 CALL DWORD PTR DS:[<&SHELL32.ShellExecuteA>] ; ShellExecuteA
0040190E |. 81C4 68010000 ADD ESP,168
00401914 . C3 RETN
The above code fragment is called subroutine. It is a set of one or more machine instructions that is called from one or more callers, i,e, memory addresses on the same program. The specific subroutine starts from address 004018C0. This means that somewhere in the program there is another machine instruction, the caller, in the form:
CALL Swlipi32.004018C0 (i.e. GOTO 004018C0).
Indeed if you search a bit we will find this:
0040277C E8 3FF1FFFF CALL Swlipi32.004018C0
What I want to do here is to make the program to ignore this instruction. But how? The answer to my problem is called (in assembly language terms) NOP, which means No OPeration (http://en.wikipedia.org/wiki/NOP). I am going to replace the current instruction with one or more NOPs. At the end, the instruction of the address 0040277C will be:
0040277C . 90 NOP
0040277D . 90 NOP
0040277E . 90 NOP
0040277F . 90 NOP
00402780 . 90 NOP
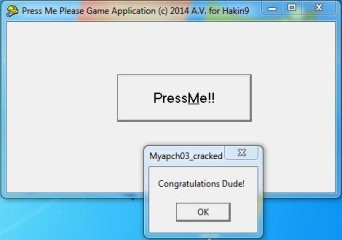
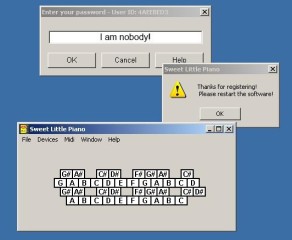
In case that you wonder, why our initial one instruction becomes five instructions, please note that we must always keep the size of the initial instruction when we replace. Since each NOPs requires just 2 bytes and the initial instruction was 10 bytes long then we had to repeat the NOP, five times! Clever huh? To be honest, such specific tasks (nowadays) performed automatically by all good debuggers and of course Olly is one of them! Our final task is to save my changes to a new executable, the cracked one. So, I press Right Click | Copy to executable | All Modifications: A new window appear, I just press Copy All. A new window appears (again) that shows our modified assembly code. I close this window and a new one appears (again!! – I promise this is the last one!) that prompts me to enter the new executable filename. I enter “Swlipi32_Cracked.exe” and then OK! That’s it! When I start the application I see the desired results (Figure 6).
Figure 6. Our cracked Sweet Little Piano
Please note that this specific method in reverse engineering world is called patching (http://en.wikipedia.org/wiki/Software_cracking). It is considered as the most quick and dirty way to overcome a protection. From the “reversing science” point of view it is also considered as the less knowledgeable method, since it does not require a lot of effort (or knowledge). Nevertheless it is a required elementary step in order to be a good reverser.
As you see, we just scratch the iceberg’s tip. Nowadays cracking is a lot more difficult even with the excellent cracking tools of the net or of the dark-net. Companies and programmers (hopefully!) are now more suspicious about cracking. New methods have been invented and new protections (packers, interrupt checkers, obfuscators etc). On the other hand, remember that what locks can be unlocked…
No comments:
Post a Comment