Let me start by sharing a little bit of programmers humour: some programmers decided to humour us and inserted the following text when something goes wrong with our Youtube request (500 Internal error) – “Sorry, something went wrong. A team of highly trained monkeys have been dispatched to deal with this situation.”
Now, you are probably asking: what does this have to do with Wi-Fi hacking? Are we hacking Youtube? NO! Is the solution to Wi-Fi hacking in Youtube? Probably! But this article is not about that. This article is about how we can efficiently hack Wi-Fi networks WPA2 protected in an efficient way.
So where do the trained monkeys and the Wi-Fi networks combine? First, Youtube is massive, a lot of code and systems on distributed infrastructures; second, it’s highly unlikely that one error spotted by a user might be spotted by any system admin or programmer; third, even if the error is relevant Youtube will not be sending anyone to check the error physically.
What I’m saying is that a global infra-structure, such as Youtube, looks at errors on a global, performance and security scale and spans resources as required, over multiple systems, to load balance performance and security. No one really looks at specific particular cases but, instead, uses their resources solve global events that impact global cloud systems.
Based on this, I’ve decided to create a new approach to handle the WPA2 hacking process. As a Security Auditor I keep pushing reports saying that Wi-Fi can, potentially, be a weak entry point and therefore needs extra caution regarding network design. But how safely are we using a Wi-Fi network with WPA2 pre-shared key?
At this point, it’s important to notice that WPA2 as it stands, wasn’t broken. Also, we are looking at a scenario where poor Wi-Fi security measures are in place. Nevertheless, I believe that this setup counts for most of the Wi-Fi deployments out there. Also, if a protocol isn’t broken doesn’t mean it isn’t hackable. That’s what I want to show you, using a new approach, where resources are potential unlimited and cost effective.
So, how can WPA2 be hacked? We can brute force the password against the Wi-Fi network (for now, let’s keep the concept global). This has been proven time consuming and resource intensive and therefore not very effective. Let me show you why. Let’s take a look at what’s available.
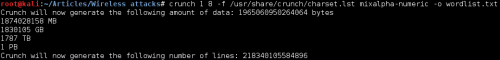
First, create a word list and brute force the handshake to death. Now, if you read a little bit about this attacks, most of them will tell you that the only way you might achieve such stunt would be to do some “reconnaissance” (like the company’s website) and use most of the words found to create a combination of words that might get you lucky. I don’t believe in luck – hackers do their own luck. So let’s see what happens when we try to create a word list that will open any network with and WPA2 key of 8 characters (Alphanumeric upper and lower case):
Figure 1. Crunch Word list creation
Whoa! There’s no way this will fit on my external hard drives. Even if we get an external source to “host” this files, we’re talking about costs “NSA style” that normal mortals won’t have to spend. I guess most readers must be thinking “What the hell is this guy doing?” I agree, but stay ‘till the end. This is just a walk into the past so we can understand the future, and believe me, it’s a bright future.
So, normal word list with Crunch is out of the question. But wait, why don’t we pipe Crunch into Pyrit anyway? Would that make a difference?
A few words about the above command: we are saying to Crunch to generate all combinations of 8 characters, where we have provided the characters to use (it’s just easier if I pick all the characters I know and it will get the job done), piping the results to Pyrit that will use them (-i -) to pass through the attack to the .cap file for the Wi-Fi test network (SSID).
As you can see around 2000 PMKs per second would take us years to brute force, making it a not so viable way to hack WPA2 Wi-Fi networks. I found this link over the internet that can explain the magnitude of time it would take – http://www.lockdown.co.uk/?pg=combi. I know that you’ll probably think this is not how you do it. You probably need to go for CUDA Pyrit. And you’re right. For now I just want to show you that the normal Desktop/laptop just won’t cut it.
There is no efficient way to do it. No efficient way on how to do it. This is the part where I lay down my method. And no, we won’t be using CUDA at this stage, since we won’t be talking about the 5 Trained Monkeys yet (and they hold hands together). So, what’s the method? And why are we using Pyrit?
The reason is simple: Pyrit uses an awesome feature that allows you to attack a capture using a pre-loaded database. And why is that relevant? Because it does it by the millions per second, and because we can start the process of “our rainbow” tables. In one word, it ESCALATES. Meaning we can potentially break any length WPA2 password and I always wanted to get my hands on this solutions.
So, let’s see how my “poor” laptop does when first create the words and then import them to a database.
We are still going to stick with Crunch and Pyrit. Pyrit comes with a pre-installed database out of the box that you can use. Still, I leave it to you to connect to external databases that can escalate much better than the ones on my PC.
Based on what we did previously, we’ll going to make this in 3 steps:
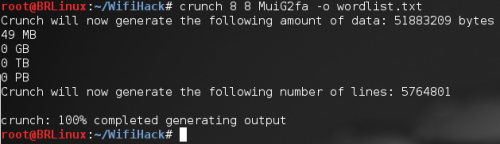
• Create the word list based on the same characters used before
Figure 2. First step
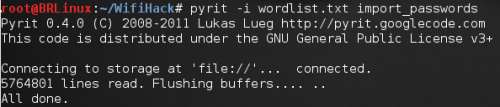
• Upload the word list to Pyrit DB – we are going to give a value to option -i in Pyrit
Figure 3. Second step
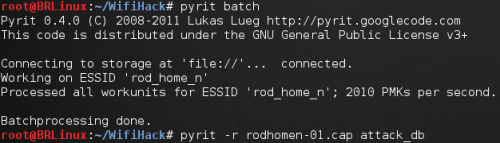
• Create the batch and attack
Figure 4. Third step
As you can see, the process is quite fast after we get the batch running. Still, the batch took about the same time to run than the pipe approach, so it still doesn’t give me the flexibility and scalability I want as a hacker. I want to be able to do it in a couple of hours maximum and be able to escalate the number of characters in the combinations in a near future.
So, the next normal step is for us to arrange for computing power. In reality that’s what’s lacking right now: get the batch process to be faster (we still need to figure out the amount of data generated by Crunch as seen in the beginning of this article, but we’ll get there later). Should we be thinking of going right now to Amazon and buy the new brand PC with a powerful Nvidia card? Well we could but I’m not sure how that can be a scalable flexible solution.
On the topic of Amazon and back with the five trained monkeys… How about getting a solution that scales, and is flexible, cost effective and, like the trained monkeys, will do the work on a scale that no one can actually control? It’s time to bring out the big guns and get the Ferrari out. At least rent one.
I give you EC2 AMIs. Amazon just roll out a couple months ago some AMIs dedicated to high processing performance, based on the use of GPUs instead of CPUs (that will get the job better done), at a fractional hourly price that we can afford. I give you the G2 instances. And yes, now the trained monkeys are in control.
[raw] [/raw]
As you can see, for less than a dollar for one hour we get a machine with all the power we need. I must say, that it took me a while to get the username (ec2-user) for the AMI, stating here – Amazon it’s NOT CLEAR what’s the user name. Never the less, got it running and updated and you won’t believe how fast it was – 22Mbs bandwidth and a lot of processing power.
Regarding Amazon AMIs, I could take all article and expand on this, since there’s a lot to say. Nevertheless, it’s up to you to understand the different options available and instances that you can use. Also, remember that not all instances are available worldwide. Not that I think that region would be important on the hacking we are doing. Most of the information I found online points for the use of Amazon own AMIs. Again, it’s up to you.
Figure 5. Amazon Lnux AMI with NIVIDA GRID GPU Driver
The AMI we are using comes empty and, therefore, we need to put all that tools we require in.
For a job well done, we’ll require Python 2.5, CUDA Pyrit and Crunch. Only then we’ll be able to put this baby to the test. For now, I’ll assume that you, the reader, have the knowledge to do the above or, at least, have a Master in Google search, where you can find all the information you require doing it.
This article is not about getting Crunch and Pyrit and, therefore, I won’t go deep into it. Let’s just say that some users out there did us the favour of compiling some interesting scripts that will allow us to get Pyrit (and some other bonus tools) up in running in seconds. That’s the power of the AMI: huge bandwidth and computer power.
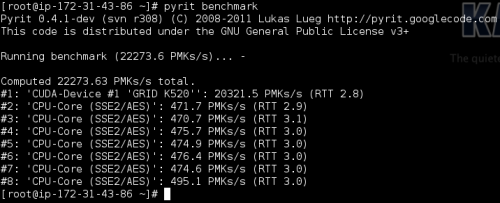
For performance’s sake, I’ve decided to run Pyrit benchmark test and the results are just awesome.
Things are looking good. We should now see how much faster we can crack our test network. First I’ll pipe Crunch to Pyrit and then I’ll use the built-in database to attack the .cap file.
Figure 6. Attacking the .cap file
We finally got where we need to reset our mind. I’m telling you this because you, reader/hacker, by now, saw that all the methods used won’t actually solve our problem. We still can hack into, potentially, any WPA2 passphrase length. It still takes too much time and, therefore, it doesn’t escalate. Untill now, and you’ll find some documentation online about this, all theories point to the use of Crunch to create a huge word list and Pyrit, using distribution loads to other AMIs. Now I didn’t talk about this because I still believe that won’t make it anyway.
About that reset and the 5 monkeys, let’s see what the Cloud can provide us (and by cloud I here launch
the next Quest – on what other clouds did you were able to run the same project? Send me your feedback for I am anxious to know). It gives us the flexibility by allowing us to use worldwide multiple AMIs or VMS;
It allows us to just pay by the hour usage, so we can actually turn off and leave it off ‘till we need to use it; It allows us to create a machine, leave it off with no charge associated and create new VMS from it.
The last paragraph it’s of the upmost importance. Let’s try to do a mental game and see how we can use all the tools described ‘till now and combine them with the advantages mentioned above. Did you get there? Need 5 more minutes? Let me help you structure your mind and define a new strategy for WPA2 cracking.
What if we could break the Crunch/Pyrit process in small bits and still use the DB feature that allows us to attack much faster? That would mean creating multiple VMS pre-loaded with Pyrit and a small part of the word list/database loaded onto it. That means that by running multiple VMS we’ll be able to crack the WPA2 in a short period, since each VM is just processing part of the load. By the end, all the VMS have processed all the possible combinations. Also, this method will allow us to escalate as far as we can go. We just need to add a new VM or VMS that will ease the load on the other machines. And for the hourly cost, believe me, we can grow and grow. Besides that, we can use the power of templates, so we don’t have to start from scratch every time we need to crack a Wi-Fi Network. The batch still needs to run, since the SSID will change, but the password list that each VM has loads and all the work required can be done prior to any hacking.
The storage problem is also gone. Load and space we can escalate, giving us the cost flexibility we need.
We just need to do our homework prior to loading the .cap file, set the SSID and run the batch. The password list will be already pre-loaded on the template from where we create the VM.
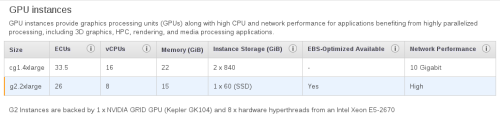
Technically speaking, let’s walk step by step so you can see the wonders of what we are doing. This time, and because I’ve already mention it, I’ve decided to go with a different AMI so you can see the different options available. Also be careful about the example you choose, as many options have different prices and performances. I went with an AMI from Amazon GPU prepared and the g2x2large example – more expensive but definitely worth it.
Figure 7. GPU instances
Step one
get the right tools for the job. Again, I won’t waste time here since I believe that the hackers that kept reading until now understand the power of Google and will be able to do this in a heartbeat. Remember that this won’t be your production machine but, instead, a template we are creating so we don’t have to do part of the process every time we want to hack a Wi-Fi network. Also, it will allow us to construct our 5 Monkeys model, where resources are spanned and not physical.
Step two
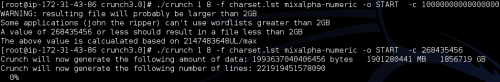
Create a small fraction of the word list. Now, this is where it got trick. Never the less and after going through Crunch manual we figure out a way to break the word list in small pieces. It actually breaks it to a maximum file size and gives it a name, allowing us to re pick where it stopped and create from there on. If you notice the -c option you’ll see I’ve chosen a huge value so Pyrit could actually tell me which maximum value I should use.
Figure 8. Pyrit warning
In this example we’ll be creating all combinations, upper and lower cases, with all the numbers 1 to 8 characters. As you can see Crunch will be responsible for creating the file names. We’ll then change the command to re-pick where Crunch left off and start creating a new set of files. He just needs to keep an eye for the number and size of files created and stop before we run out of space. Then, we just launch a new VM when we want to continue and start from where we left off. We’ll just going to overlap the last file created.
Figure 9. Crunch
Pay attention to the last sequence in file name: xxxxx-yyyyy.txt. You’ll need to correct the minimum number of characters on the crunch command to match the number of yyyyy.
Step three
Upload all the files to Pyrit database. Another way you have to do it, would be to generate the word files on your local computer and upload them to the VM. You have the bandwidth so why use the storage for more than a database. This way you won’t take space with useless files. You’ll upload to one VM and place it directly on Pyrit and do a manual distribution to other VMS. You can schedule the time and leave it running during the night, since you’ll probably have more cheap storage attached on your computer.
Step four
Save the VM as a template. This step is pretty easy and straightforward. You just go to your EC2 management console, choose the instance you want (in this case all the instances created are pre-loaded with the word lists) give it a name (my advice would be to choose something like nameoffirstfile-nameoflastfile so you know what this VM is supposed to process) and choose “create image.”
Step five
Launch all the instances, insert the ESSID in Pyrit and run the batch.
Step six
Upload the cap file and attack it with Pyrit DB. I just want to add a note off-topic in this step (I’m using an Android application on my phone called Linux Deploy that allow us to install Kali Linux ARM version pretty easy). You can then, when walking down the street, get a perfect cap file for the handshake of any Wi-Fi network that you encounter, scp the file to Amazon cloud and let the Monkeys do the work for you. After all they are trained.
You’ll notice that all the steps might take some time, like the word creation, VM creation and upload to Pyrit database but in fact you just doing it once, saving it as a template and creating new VMS from the ones previously created. It will take you some time, but you’re doing a kind of Rainbow tables for Wi-Fi so expect some work prior to attack and cracking.
As you can see, all the tools and servers mention are not new to us, Hackers. It’s a matter of using some of the available tools and redefine the strategy we will use to attack whatever we can attack, make it more efficient and faster. My challenge here was to see how the mental process can be built and hope that the readers might think about other attacks or hacks that although being new, with a different strategy, might get you in where it wasn’t possible before.
New tools, new clouds and processing power will keep emerging and we hackers have to start thinking how we can leverage a good technology and give it the power it needs to achieve what we want. Also, this strategy defined here will probably go undetected. The capture and the cracking occur in different moments, and the cracking itself won’t raise any flags anywhere. Not even on Amazon.
I just hope that if you Security Guys from Amazon are reading this, that you understand that we won’t be using this for bad things. Keep in mind that we should only use this technique for Authorized testing or educational purposes. Always get permission or use your own network, before you start cracking.
No comments:
Post a Comment